Strategic threat analysis is heady stuff. But so is futures work. Or fat-tails analysis.
Threat assessments and predictive estimates easily rank among the most demanded analytic products, particularly in strategic intelligence or foreign affairs analysis.
On this page we will periodically publish Case Studies that demonstrate the use of different Structured Analytic Techniques for analysis of real-world issues.
Some of the case studies are our own, designed for use in our course.
Others are those handed in by our students as course Home Projects. They are published with authors’ permission as submitted and graded, without any editing on our part.
We find it truly impressive – and motivating – to see how students previously unfamiliar with SATs climb a very steep learning curve to produce work of such a high quality.
Either way, our case studies are intended to be both educating and captivating reading. Enjoy!
And by all means, leave your comments. Please be specific and succinct in your criticism (and praise). Show respect in order to be treated with respect.
To receive alerts whenever we publish a new case study, please subscribe to our newsletter.
commentNo Comments
2020 data on Afghan opium poppy cultivation baselines results of drug control efforts during the past 19 years. After the Taliban has just become before the Taliban. Key findings. Statement of the problem. Description of the analytic method. Applying the method to the problem. Endnote. Researchers and business analysts have studied Afghan opium poppy cultivation…
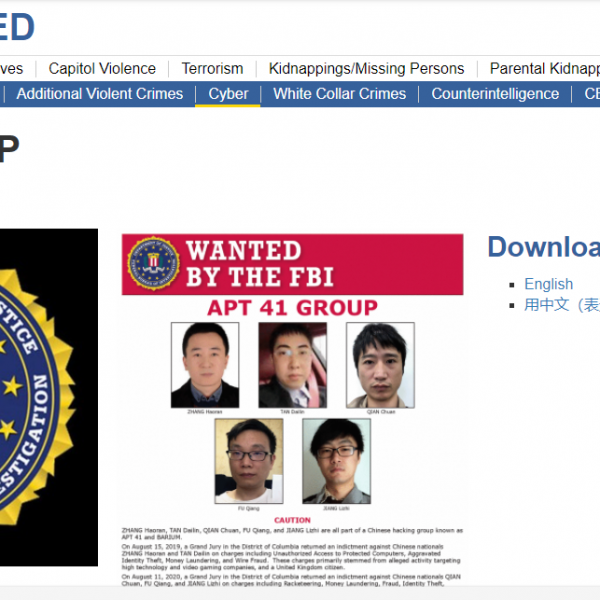
Ranking FBI Most Wanted cyber threat actors
comment1 Comment
Ranking FBI Most Wanted cyber threat actors puts APT10 in the top slot. Or does it, really? Well, it all depends on how you look at it. 51 graduate students from 12 countries took part in ranking FBI Most Wanted cyber threat actors. They used a range of structured analytical techniques that included pair ranking…
Right-wing UK extremist threat ranking using 11 variations of the Long Matrix
commentNo Comments
Right-wing UK extremist threat ranking suggests an omission in Government policies. This analysis posits that the “Britain First” organisation takes the top slot in right-wing UK extremist threat ranking. Findings suggest a possible omission in UK anti-extremist policies. While the “National Action” organisation is proscribed since December 2016, “Britain First” remains legal. My name is…
The First Crusade – use of Multiple-Perspective Utility Analysis as a historical research method
commentNo Comments
The First Crusade – utility-based analysis as historical research method This historical research method involves use of the Multiple-Perspective Utility Analysis (MPUA), a structured analytical technique. It is novel insofar it attempts an unorthodox – past- instead of future-driven – application of MPUA. Samuele Vasapollo is a scholar of history and international relations and can…
Predicting armed insurgency threat against FORFOR troops – does reality fit the theory?
commentNo Comments
A review of data on armed insurgency threat dynamics attempts to answer this question. If armed insurgency threat to foreign troops can be predicted, deployment and exit strategy for conflict-stabilisation and peace-keeping forces may require rethinking. In an internal armed conflict, indigenous security forces and domestic insurgents will at some point collude to oust a…
Red-Teaming Korean Reunification – Buy-out, Cyber-attack, or ..?
commentNo Comments
RED TEAMING KOREAN REUNIFICATION: MULTIPLE-PERSPECTIVE UTILITY ANALYSIS FROM CHINESE ANGLE Red teaming Korean reunification can aim to identify multiple scenarios leading to a strategic change. Adding utility analysis on top can help to choose the one future among many that can accrue highest utility to the tasking authority. The technique of Multiple-Perspective Utility Analysis (MPUA)…
The Players of Games. Will EU visa policy create new strategic threats to EU?
commentNo Comments
New strategic threats to EU are coming from the most unexpected directions. I don’t mean COVID19. That has been a “black swan”. I mean what’s coming next. At the time of this writing (mid-April 2020), EU institutions have been largely reduced to irrelevance. It’s not that their response to the COVID-19 crisis was weak or…
Spot-on Election Forecasting Using Analytic Failure Simulation Technique
commentNo Comments
Election forecasting is one core occupation of policy analysts all over the world. Analytic Failure Simulation is a structured analytic technique that can increase the accuracy of estimates. And as a consequence, raise analyst credibility. Election forecasting can also be great fun. I’ll show you how. Overview of the Analytic Failure Simulation Technique. Case study…
Cyber Threats Ranking Using SLEIPNIR Assessment Tool
commentNo Comments
CYBER THREATS RANKING – A NEW CHALLENGE FOR THE TRUSTED LONG MATRIX In this post I’ll show you how to produce an actionable Strategic Threat Assessment (STA) using the Sleipnir matrix. Moreover, I’ll show you how to do it using both the trusted Long Matrix 1.0 and the newer Long Matrix 2.0. And last of…
The invasion of Lampedusa. Using High-Impact Low-Probability analysis to defeat migrant smugglers
commentNo Comments
OR HOW TO THWART MIGRANT SMUGGLERS IN 7 STRUCTURED STEPS What is claimed to have never happened before, has simply not happened yet. This Case Study addresses the strategic threat posed by migrant smugglers in Southern Mediterranean. It demostrates the use of a structured analytic technique called High Impact-Low Probability Analysis (HI-LPA). The purpose of…